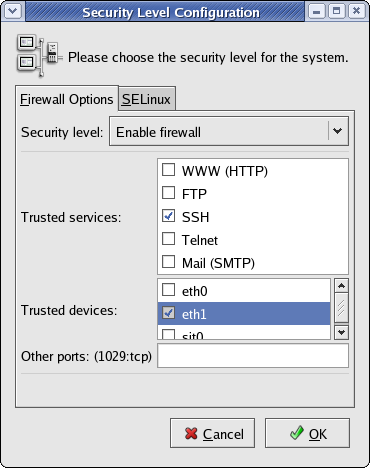
Trusted Devices
If you chose to install a firewall, you must make the private network interface (typically eth1) a "trusted device" to enable all traffic on this interface to pass through the firewall; otherwise, the cluster will not run properly. This must be done post-installation.
After you have installed Red Hat and Scyld ClusterWare, reboot the system and log in as "root".
Access the security settings through the Red Hat Applications -> System Settings -> Security Level menu options.
In the Security Level Configuration dialog box, make sure the private interface is checked in the "trusted devices" list, then click OK.

If you plan to use SSH to connect to the master node, be sure that SSH is checked in the "trusted services" list.
You are now ready to boot and configure your compute nodes; see the Chapter called Installation of the Compute Nodes.